Updated for 2025 compliance standards
In 2024 alone, healthcare data breaches exposed a staggering 276 million patient records, with small and mid-sized medical practices increasingly targeted due to weaker IT defenses and vendor vulnerabilities. According to the U.S. Department of Health and Human Services’ Office for Civil Rights (OCR), HIPAA violations can result in financial penalties ranging from $141 to over $2.1 million per year, depending on the severity and corrective actions taken.
These statistics should not be brushed off by IT professionals and compliance officers, as the stakes have never been higher. Staying compliant with the HIPAA Security Rule and Privacy Rule is vital in safeguarding your organization from devastating fines, reputational damage, and operational disruptions.
This audit-ready HIPAA IT compliance checklist provides healthcare organizations with a systematic framework for assessing, implementing, and maintaining HIPAA-compliant information systems.
Whether you’re preparing for an OCR audit, conducting an internal review, or building an IT compliance program from the ground up, this comprehensive guide will walk you through every safeguard, requirement, and documentation standard that matters in 2025.
By the end of this article, you’ll have:
- A clear understanding of current HIPAA IT requirements
- A step-by-step checklist to assess your compliance posture
- Practical tools to organize your documentation
- Recommendations for risk assessment, technical controls, and audit readiness
- A downloadable HIPAA IT compliance checklist to support your team
Let’s dive in.
Understanding HIPAA IT Requirements
HIPAA compliance for IT begins with the Security Rule, which requires safeguards to ensure the confidentiality, integrity, and availability of electronic protected health information (ePHI). While the Privacy Rule governs how PHI is used and disclosed, the Security Rule addresses the technical, administrative, and physical protections needed across your IT environment.
The Three HIPAA Safeguard Categories
2025 Regulatory Updates Affecting IT Compliance
| Safeguard Type | Description |
|---|---|
| Administrative | Policies and procedures governing workforce responsibilities and security management. |
| Technical | Technology controls to protect ePHI access and transmission. |
| Physical | Facility and device protections preventing unauthorized physical access. |
Recent HHS guidance highlights key compliance areas:
- Third-party risk: Stronger vendor oversight and Business Associate Agreements (BAAs) are critical.
- Cloud compliance: New standards for securing cloud-based ePHI and email systems.
- Ransomware defenses: Emphasis on detection and recovery capabilities.
- Mobile device security: Heightened expectations for managing smartphones, tablets, and remote access.
Common Misconceptions About HIPAA IT Requirements
- ❌ “HIPAA only applies to large hospitals.”
- ✅ Any covered entity or business associate, regardless of size, must comply.
- ❌ “Encryption is optional.”
- ✅ While labeled as “addressable,” encryption is essential unless a documented alternative provides equivalent protection.
- ❌ “Our EHR vendor handles HIPAA compliance for us.”
- ✅ Responsibility is shared. You must ensure your vendors are compliant and have valid BAAs.
- ❌ “Annual risk assessments are optional.”
- ✅ A regular, documented risk assessment is a required administrative safeguard.
The Role of IT Professionals in HIPAA Compliance
IT teams lead HIPAA implementation by managing access controls, encryption, audit logging, and secure configurations across systems. Their collaboration with compliance teams ensures both technical effectiveness and policy alignment. With HITECH expanding enforcement and penalties, staying current with evolving guidance is essential for risk reduction and audit readiness.
Administrative Safeguards Checklist
Administrative safeguards form the backbone of HIPAA compliance. These policies and procedures ensure that your organization’s workforce, oversight processes, and access controls align with technical systems to protect ePHI.
Security Management Process Requirements
HIPAA requires a formal process to assess and manage risks to ePHI. A compliant risk analysis must cover all systems, both on-premises and cloud, and be reviewed annually or after significant changes.
- Define the full scope of systems handling ePHI
- Identify threats, vulnerabilities, and impacts
- Assign risk levels and prioritize remediation
- Develop and track a mitigation plan
- Maintain documentation of methodology, findings, and updates
- Review audit logs regularly and enforce a sanction policy for violations
💡 Compliance Tip: A checklist is not enough. OCR requires documented risk assessment processes, including risk matrix and rationale. Use NIST SP 800-30 or HHS’s official guidance.
Workforce Security Measures
Workforce access must be authorized, supervised, and promptly removed when no longer needed. In today’s remote environments, policies must also address remote work and BYOD.
Checklist:
- Role-based access controls
- Remote access and VPN usage policies
- BYOD policy with encryption and remote wipe
- AUP signatures and MDM enrollment
- Termination procedures with immediate access revocation
- Access logs and modification tracking
💡 Compliance Tip: Make BYOD and remote work policies part of the standard access authorization workflow to ensure full coverage.
Information Access Management
Covered entities must implement policies that define who has access to ePHI, under what conditions, and how access is granted, modified, and revoked.
Checklist:
- Maintain documented access request and approval procedures
- Use unique user IDs and authentication controls
- Implement session timeout settings
- Conduct quarterly access reviews and audit trails
💡 Compliance Tip: Use access logs and audit trails to verify that permissions align with actual job duties and limit “privilege creep.”
Administrative safeguards form the structure that supports effective technical and physical controls. They must be documented, maintained, and retained for at least six years.
Technical Safeguards Checklist
Technical safeguards are the HIPAA-required technology controls that protect electronic protected health information (ePHI). These measures limit unauthorized access, maintain data integrity, and secure information during storage and transmission.
Access Control Requirements
HIPAA mandates that only authorized individuals can access ePHI. Your systems must enforce strict access policies using authentication, role-based permissions, and session management.
Checklist:
- Assign unique user IDs for all users
- Enforce strong passwords (12+ characters, mixed-case, number, symbol; prevent reuse of last 6)
- Require multi-factor authentication (MFA) via one-time-password apps, smart cards, or biometrics
- Configure automatic logoff after 15 minutes of inactivity
- Establish emergency access protocols
- Restrict access based on roles and minimum necessary principle
- Require re-authentication after VPN or session timeouts
- Use access control lists (ACLs) to manage permissions
💡 Compliance Tip: Document your MFA setup and timeout policies. Screenshots and config logs help demonstrate compliance during audits.
Audit Controls
Audit controls track access and activity in systems that store or process ePHI. These logs help detect unauthorized behavior and support incident investigations.
Checklist:
- Log key events: logins/logouts, file access/modifications, permission changes, and data transfers
- Include key log fields: timestamp, user ID, action taken, system/file accessed, success/failure, IP address
- Retain logs for at least 6 years
- Review high-risk system logs weekly; lower-risk monthly
- Automate alerts for unusual activity (e.g., multiple login failures, bulk file access)
- Store logs in tamper-proof, access-controlled systems
💡 Compliance Tip: Use a SIEM platform (e.g., Wazuh, Microsoft Sentinel) to centralize and analyze logs in real time.
Integrity Controls
Integrity safeguards ensure ePHI is not improperly altered or destroyed. These controls validate data consistency and support recovery efforts.
Checklist:
- Use SHA-256 hashes or checksums to verify file integrity
- Implement digital signatures for critical records
- Track file changes with version control
- Automate audit trails to flag suspicious modifications
- Use error detection tools to identify data corruption
- Regularly test backup restoration processes
- Define and document protocols for error correction
💡 Compliance Tip: Add integrity checks to your backup routines. Verifying restored data ensures it’s trustworthy and complete.
Person or Entity Authentication
Authentication verifies that a person or system accessing ePHI is legitimate.
Checklist:
- Require unique usernames and passwords for all users
- Enforce MFA for all endpoints accessing ePHI
- Use biometric verification or smart cards where feasible
- Track failed login attempts and respond to anomalies
- Prohibit shared credentials
- Verify the identity of external systems and vendors
💡 Compliance Tip: MFA isn’t just for VPNs. Extend it to EHR portals, admin tools, and remote desktop sessions.
Transmission Security
HIPAA requires protections for ePHI transmitted over networks. Encrypting and securing communications is essential to prevent data leaks and interception.
Checklist:
- Encrypt all ePHI using AES-256
- Use TLS 1.2+ for web traffic and encrypted email
- Avoid FTP; use SFTP or HTTPS for file transfers
- Require VPNs for all remote connections
- Enable end-to-end encryption for internal chat and telehealth platforms
- Disable outdated protocols (SSL, TLS 1.0)
- Validate SSL/TLS certificates for public-facing systems
- Inspect encrypted traffic for suspicious activity
💡 Compliance Tip: Don’t rely on default encryption settings. Validate email and EHR configurations meet HIPAA standards.
Technical Implementation Checklist (Summary)
Checklist:
- Unique user IDs and strong password policies
- Multi-factor authentication (MFA)
- Emergency access and session timeout policies
- Centralized audit logging and alerts
- Hashing and integrity validation for ePHI
- Biometric and smart card-based authentication
- TLS 1.2+ and AES-256 encryption for data transmission
- VPN access required for remote staff

Physical Safeguards Checklist
While HIPAA is often associated with digital security, physical safeguards are just as critical. These controls protect access to buildings, workstations, and equipment that store or process ePHI. They help prevent unauthorized access, tampering, and damage from environmental threats.
Facility Access Controls
Covered entities must limit physical access to locations where ePHI is stored, such as server rooms and networking closets, while ensuring authorized personnel can perform necessary duties.
Checklist:
- Use badge or keycard systems for sensitive areas
- Maintain visitor logs with sign-in/out times and escort protocols
- Restrict server room access to designated IT/security staff
- Install video surveillance at critical entry points
- Configure alerts for after-hours door access or forced entry
- Require two-factor entry (e.g., badge + PIN or biometric) for data rooms
- Apply environmental protections:
- ○ Fire suppression (e.g., FM-200 systems)
- ○ Water leak sensors under raised floors
- ○ Battery backups and generators, tested regularly
💡 Compliance Tip: Conduct quarterly walkthroughs and access list reviews to ensure access privileges remain appropriate.
Workstation Security
Workstations must be positioned and configured to prevent unauthorized viewing or access to ePHI in both clinical and administrative settings.
Checklist:
- Face monitors away from public view
- Install privacy screens on devices with ePHI access
- Enable automatic screen lock after 5–10 minutes of inactivity
- Require unique user logins; no shared credentials
- Use cable locks or docking stations for portable devices
- Enforce a clean desk policy:
- ○ No unattended printouts
- ○ Locked drawers for sensitive materials
- ○ Secure storage for portable drives
💡 Compliance Tip: Review workstation layouts and signage annually to confirm HIPAA visibility standards are met.
Device and Media Controls
Proper management of devices and media that store ePHI, from acquisition to disposal, is required under HIPAA.
Checklist:
- Maintain a full inventory of devices with tracking info
- Assign responsibility for lifecycle management
- Use appropriate destruction methods:
- ○ Shred, degauss, or NIST-wipe hard drives and flash media
- ○ Factory reset and remote wipe mobile devices
- Require sign-in/out logs for off-site equipment
- Encrypt all removable media
- Store backups securely, on-site and with HIPAA-compliant off-site vendors
💡 Compliance Tip: Document all disposals with serial numbers and certificates of destruction.
Real-World Example: Physical Safeguards in Action
A multi-site dermatology practice implemented role-based badge access to restrict entry to server closets and prescription printing stations. Visitor logs were digitized with tablet-based sign-in, and all workstations in exam rooms were equipped with privacy screens. Quarterly audits revealed that one backup drive was stored at an unapproved site—corrective action included revising the backup policy and retraining staff.

Documentation and Policy Requirements
In HIPAA compliance, if it’s not documented, it didn’t happen. Documentation serves as both evidence for auditors and a practical guide for how your organization manages ePHI. Even strong technical controls can fail an audit without corresponding, well-maintained documentation.
Required HIPAA IT Policies
Covered entities must implement and maintain written policies covering key areas of HIPAA IT compliance:
- Security Management Policy – Defines risk analysis, mitigation, and incident response procedures.
- Access Control Policy – Describes how ePHI access is granted, modified, and revoked.
- Workforce Security Policy – Outlines workforce onboarding, supervision, and termination processes.
- Incident Response Policy – Details how incidents are identified, contained, and resolved.
- Backup & Disaster Recovery Policy – Covers frequency, storage, recovery testing, and responsibilities.
- Device and Media Control Policy – Guides the handling and destruction of hardware storing ePHI.
- Workstation Security Policy – Describes acceptable use and physical security standards.
- Transmission Security Policy – Identifies required encryption methods for data in transit.
- Vendor Management Policy – Requires BAAs and oversight for third-party vendors.
💡 Compliance Tip: Include version numbers and revision history to demonstrate ongoing policy review.
What to Include in Each Policy Document
Each policy should contain:
- Policy name, version, and effective date
- Purpose and scope
- Roles and responsibilities
- Definitions of key terms
- Procedures to be followed
- Applicable regulations (e.g., HIPAA Security Rule citations)
- Documentation and audit references
- Review and revision schedule
Retention and Accessibility Requirements
HIPAA requires policy and risk assessment documentation to be retained for at least six years from creation or last effective date. Acceptable formats include:
- Encrypted electronic documents (e.g., PDF, Word)
- Secure cloud storage with version history
- Locked physical filing systems
Make policies easily accessible via your intranet, training portal, or onboarding materials.
💡 Compliance Tip: Store documentation in a centralized, access-controlled repository with audit logs to track edits and access.
Documentation Framework and Organization
A well-organized documentation system makes audits and internal reviews easier, while also ensuring that your team can quickly find and reference the necessary policies and records to maintain security and compliance.
Create a structured folder system, whether on a secure internal server, in a cloud storage solution, or within a governance platform, that mirrors the categories outlined in the HIPAA Security Rule. This approach provides clarity and improves accountability. Each folder should contain the most up-to-date documents, labeled with version numbers and effective dates. A sample folder structure might look like this:
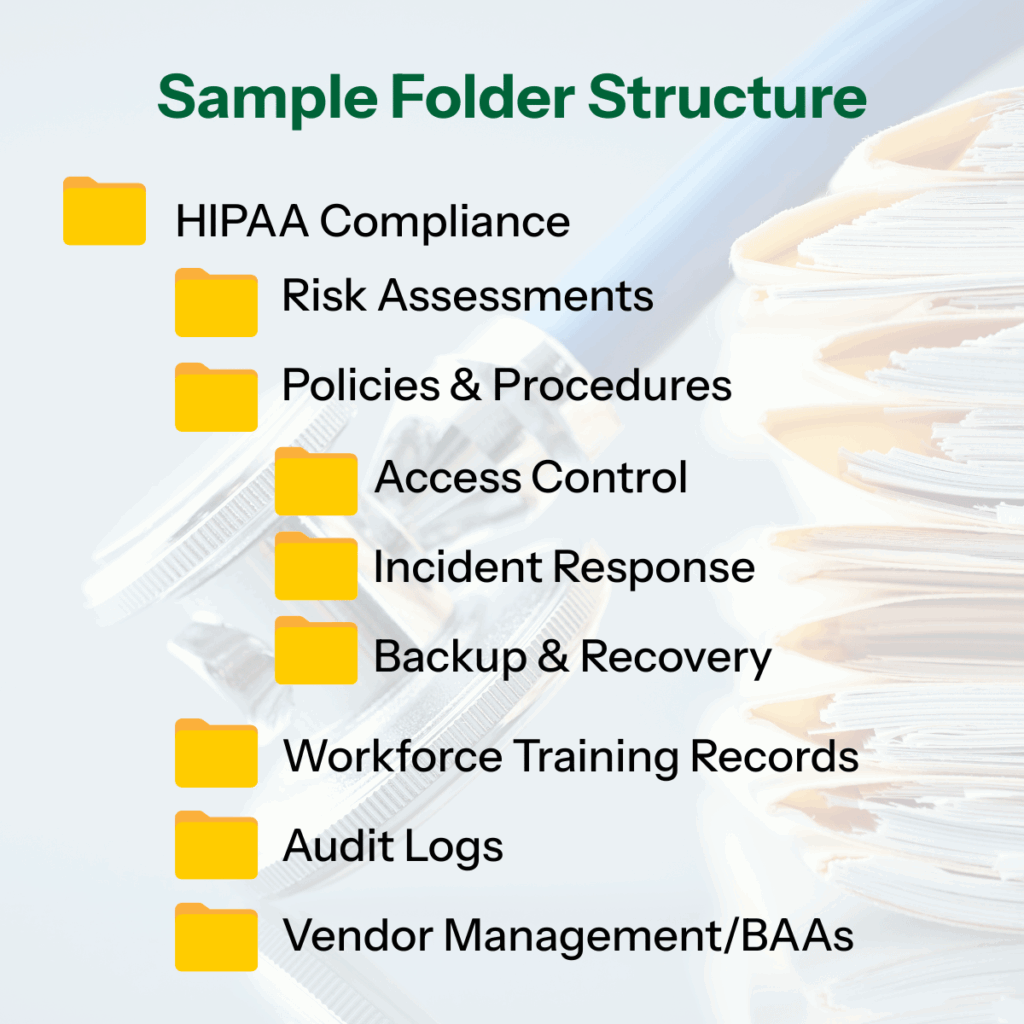
Maintain a master index or policy register at the root level of the folder system. This index should list each HIPAA-related policy, its effective date, the last review date, responsible parties, and a status column for tracking updates or pending revisions. A spreadsheet or simple table format works well for this purpose.
All documents should follow consistent naming conventions, include version control (e.g., v1.3), and indicate who approved the policy. This level of organization helps demonstrate diligence and reduces the risk of outdated or incomplete policies being relied upon.
💡 Compliance Tip: Use tools like SharePoint or GRC platforms with version control to track edits and maintain audit readiness.
Risk Assessment and Management Framework
A risk assessment is a required HIPAA safeguard, not just a best practice. Covered entities and business associates must regularly evaluate risks to the confidentiality, integrity, and availability of ePHI. To be compliant, your process must be thorough, repeatable, and documented.
Step-by-Step Risk Assessment Process
- Scope Definition – Identify all systems and workflows handling ePHI (e.g., EHRs, mobile devices, cloud services).
- Data Collection – Gather technical and procedural info via interviews, scans, and reviews.
- Threat Identification – List potential threats (phishing, ransomware, insider misuse, system failure).
- Vulnerability Assessment – Identify weaknesses like outdated software, weak passwords, or poor physical security.
- Impact Analysis – Assess the potential severity of each threat (e.g., financial, legal, clinical harm).
- Likelihood Determination – Estimate the chance of occurrence based on system use and history.
- Risk Level Calculation – Combine likelihood and impact to rank risks.
- Mitigation Planning – Prioritize remediation actions, assign owners, and define timelines.
Risk Prioritization Matrix Template
Use a color-coded matrix like the one below to visually rank risks and drive mitigation priorities.
| RISK | IMPACT | LIKELIHOOD | RISK LEVEL |
|---|---|---|---|
| PHISHING EMAIL ACCESS | High | High | Critical |
| LOST MOBILE DEVICE | Medium | High | High |
| SERVER MISCONFIGURATION | High | Medium | High |
| OUTDATED ANTIVIRUS | Low | High | Medium |
Frequency and Monitoring
Annual risk assessments are required; however, it is recommended that they be performed twice a year or after any major IT change, breach, or regulatory update. It is also important to implement ongoing monitoring, including internal audits, monthly log reviews, real-time alerts, and policy reviews.
Recommended Tools
- HHS SRA Tool – Free, OCR-endorsed
- NIST SP 800-30 – Widely used framework
- SentinelOne, ThreatLocker, Wazuh, Zabbix – Automated compliance platforms
- Qualys, Nessus – Vulnerability scanners
💡 Compliance Tip: Pair your risk assessment with a technical vulnerability scan—many insurers now require both.
Documentation Checklist
Checklist:
- Methodology and scope
- Threats and vulnerabilities
- Risk ratings and prioritization
- Mitigation plans
- Review triggers and approval
Breach Notification and Incident Response
Despite strong safeguards, security incidents can still occur. HIPAA requires covered entities and business associates to maintain a documented process for identifying, responding to, and reporting breaches of protected health information (PHI).
A breach is defined as the acquisition, access, use, or disclosure of PHI in a way that compromises its privacy or security. If an organization cannot demonstrate a low probability of compromise through a formal risk assessment, the incident must be treated as a breach.
💡 Compliance Tip: Engage a breach coach BEFORE an incident occurs. A breach coach is a legal expert who coordinates response efforts and helps reduce legal and regulatory risk. Watch our video to learn more.
Incident Response Steps
Incident Response Steps:
- Detect & Report – Monitor systems and encourage staff to report suspicious activity
- Contain – Isolate affected systems, accounts, or networks
- Eradicate – Remove threats and patch vulnerabilities
- Recover – Restore clean backups, verify system integrity
- Analyze – Perform root cause analysis and update policies
💡 Compliance Tip: Keep your plan easily accessible and review it annually or after any incident.
Staff Training and Awareness
Your workforce plays a critical role in early breach detection. To stay compliant:
- Include breach scenarios in HIPAA training
- Post quick-reference reporting guides in key areas
- Assign a clear internal point of contact for incident reporting
- Run annual tabletop exercises to test readiness
Documentation Requirements
HIPAA requires documentation for every security incident, even if it doesn’t result in a breach. Your records should include:
- Date/time of detection
- Description of the incident
- Systems and users involved
- Risk assessment results
- Containment and recovery steps
- Root cause and corrective actions
💡 Compliance Tip: Store documentation with your risk assessment and audit logs to maintain a complete compliance trail.
IT Compliance Audit Preparation
Preparing for a HIPAA IT compliance audit goes beyond collecting paperwork. It requires demonstrating a proactive, risk-based approach to safeguarding ePHI.
Start by categorizing compliance tasks based on risk level:
- High – Gaps that expose ePHI, such as lack of MFA, missing risk assessments, or unencrypted data in transit
- Medium – Issues that reduce resilience, like outdated policies or missing BAAs
- Low – Cosmetic or minor process issues, such as inconsistent policy formatting
💡Compliance Tip: Tackle high-risk items first, especially those previously flagged in audits or by your cyber insurance provider.
Phased Implementation Timeline
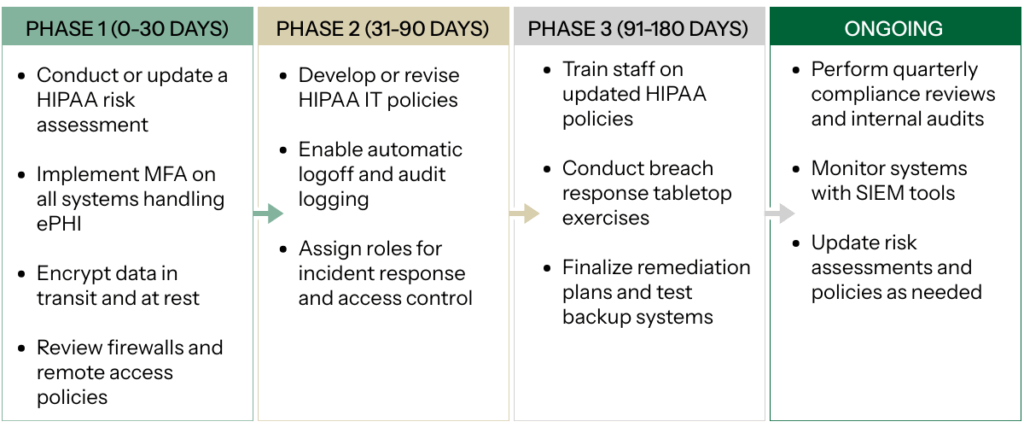
Phase 1 (0–30 Days)
- Conduct or update a HIPAA risk assessment
- Implement MFA on all systems handling ePHI
- Encrypt data in transit and at rest
- Review firewalls and remote access policies
Phase 2 (31–90 Days)
- Develop or revise HIPAA IT policies
- Enable automatic logoff and audit logging
- Assign roles for incident response and access control
Phase 3 (91–180 Days)
- Train staff on updated HIPAA policies
- Conduct breach response tabletop exercises
- Finalize remediation plans and test backup systems
Phase 4 (Ongoing)
- Perform quarterly compliance reviews and internal audits
- Monitor systems with SIEM tools
- Update risk assessments and policies as needed
Budget and Resource Planning
Consider allocating budget for:
- External risk assessments or consulting
- Security tools (MFA, SIEM, encryption, backup) — learn more
- Training platforms and policy documentation systems
| FUNCTION | RESPONSIBILITY |
|---|---|
| IT/SECURITY | Technical safeguards, logging, access |
| COMPLIANCE/PRIVACY | Policies, training, audit prep |
| HUMAN RESOURCES | Onboarding protocols, training records |
| LEADERSHIP | Oversight, risk acceptance |
Key Performance Indicators (KPIs)
Track metrics such as:
- Percentage of systems protected by MFA
- Percentage of staff trained within 30 days of hire
- Number of open risks from last assessment
- Average time to revoke terminated user access
- Frequency of log reviews
💡Compliance Tip: Align KPIs with OCR audit expectations, especially access control and incident response.
Conclusion
Achieving HIPAA IT compliance isn’t about checking boxes. It’s about protecting your patients, your reputation, and your organization’s future. This audit-ready HIPAA IT compliance checklist provides your team with a structured and systematic approach to assess and enhance your security posture.
HIPAA compliance is not a one-time project. It’s an ongoing process of risk management, staff engagement, technical vigilance, and operational discipline.
At MIS Solutions, we specialize in helping healthcare organizations design and maintain IT systems that support both security and compliance. Whether you need support with risk assessments, policy documentation, or technical implementation, our team is here to help.
Download our HIPAA IT Compliance Checklist for a printable, step-by-step version of this guide.
Ready for a compliance consultation? Contact us today to schedule a discovery call with our HIPAA compliance experts.
Additional Resources
To help you continue building a strong, audit-ready HIPAA compliance program, we’ve compiled trusted tools, government resources, and industry associations that provide up-to-date guidance and support.
Official HHS Resources
- HIPAA Security Rule Guidance Material
Clear explanations and implementation tips directly from HHS.
- Breach Notification Rule Summary
Defines breach requirements, timelines, and reporting steps.
- Risk Assessment Tool (SRA Tool)
Free downloadable tool for small- to mid-sized healthcare providers to conduct HIPAA-compliant risk assessments.
- HIPAA Administrative Simplification Regulations Text
Full regulatory text of HIPAA Security and Privacy Rules.
- OCR Audit Protocol
The exact checklist used by auditors during official OCR HIPAA audits.
Recommended Compliance Tools
- SentinelOne. A next-generation antivirus plus EDR solution for threat detection, response, and rollback at endpoint level.
- ThreatLocker. Implements zero trust through application control, storage control, and ringfencing.
- KnowBe4. Security awareness training and phishing simulation platform tailored for healthcare organizations.
- Wazuh. Includes file integrity monitoring, intrusion detection, vulnerability assessment, and built-in compliance modules (PCI, HIPAA, etc.)
- Zabbix. Tracks servers, networks, and applications via metrics and alerts.
Healthcare IT Security Associations
Provides the HITRUST CSF—a certifiable framework that incorporates HIPAA, NIST, and more.
2. Healthcare Information and Management Systems Society (HIMSS)
Offers cybersecurity best practices, vendor vetting guides, and education resources.
3. International Association of Privacy Professionals (IAPP)
Provides training, certifications, and updates on privacy laws, including HIPAA and beyond.
Whether you’re facing an upcoming audit, need to assess your current posture, or want a trusted IT partner to guide you, our team is ready to help.

