An IT risk assessment is the structured process of identifying, evaluating, and prioritizing threats and vulnerabilities that could negatively impact an organization’s information systems and data. This security risk assessment plays a foundational role in strengthening cybersecurity and achieving compliance with industry regulations.
Cyber threats are evolving faster than ever. According to recent data, a cyberattack occurs every 39 seconds on average, and ransomware attacks surged by 400% year over year in 2024 alone (Keepnet Labs, 2025). With digital infrastructure now central to business operations, no organization, regardless of size or industry, is immune.
As threat actors become more sophisticated and the cost of breaches climbs, conducting regular IT risk assessments has shifted from best practice to business-critical. Without a clear understanding of your vulnerabilities and risk exposure, you can’t effectively defend against attacks or meet today’s strict regulatory standards.
In this guide, we’ll walk you through the 9-step IT risk assessment process as a critical component of your overall risk management process. Whether you’re an IT pro refining your internal processes or a business leader seeking clarity, this article will help you protect what matters most.
Watch this VIDEO for more information about IT Risk Assessments.
Why IT Risk Assessments Are Non-Negotiable in 2025
In an era where the average cost of a data breach has hit $4.8 million globally (IBM, 2024), skipping IT risk assessments isn’t just risky—it’s reckless. These assessments aren’t just check-the-box exercises. They’re a critical part of maintaining operational resilience, meeting compliance obligations, and making smarter business decisions.
Regulatory Requirements
Regulations across industries require formal IT risk assessments, and the penalties for non-compliance are steep:
- GDPR (General Data Protection Regulation): Requires organizations handling EU citizen data to assess risks to data privacy and implement safeguards.
- PCI DSS (Payment Card Industry Data Security Standard): Mandates risk assessments to protect cardholder data and prevent breaches.
- HIPAA (Health Insurance Portability and Accountability Act): Requires healthcare organizations to conduct periodic risk assessments to protect patient health information.
- SOX (Sarbanes-Oxley Act): Public companies must evaluate and report on the effectiveness of IT controls tied to financial reporting.
- CMMC 2.0 (Cybersecurity Maturity Model Certification): Contractors in the Department of Defense (DoD) supply chain must demonstrate risk management practices aligned with their certification level.
These standards emphasize not only the need for risk assessments but also for documentation, continuous improvement, and timely response.
Financial Impact
Beyond fines and remediation costs, data breaches cause cascading financial pain. According to Keepnet Labs, 60% of small companies go out of business within six months of a cyberattack. That’s not just the breach itself. It’s the downtime, forensic investigations, legal defense, customer churn, and long-term reputational damage that bleed budgets dry.
Even a short disruption in service can have six-figure consequences. And with cyber insurance premiums on the rise, underwriters increasingly expect proof of robust risk assessment practices before offering coverage.
Operational Benefits
Risk assessments do more than identify threats; they improve how your organization operates. By pinpointing vulnerabilities, you can:
- Deploy security resources more efficiently
- Strengthen weak areas before they’re exploited
- Build faster, more effective incident response plans
- Reduce redundant or outdated technologies
In short, it’s about working smarter, not harder. According to IBM, companies with well-tested incident response plans and regular risk assessments saw breach costs that were $1.49 million lower than those without them.
Strategic Advantages
An IT risk assessment gives senior management and decision-makers data to guide strategic initiatives. Whether you’re evaluating a new vendor, expanding cloud infrastructure, or launching a new product, risk insights can:
- Influence investment decisions
- Uncover blind spots before audits
- Support long-term business continuity planning
The best decisions come from clear visibility, and risk assessments provide exactly that.
The Anatomy of an Effective IT Risk Assessment
A strong IT risk assessment doesn’t happen by accident. It’s built on a few foundational concepts that guide the entire process. To evaluate and manage risk effectively, every assessment should consider the following components: Threats, Vulnerabilities, Impact, and Likelihood
Threats
Threats are any events or actors—internal or external—that could exploit a weakness in your environment and cause harm. They can come from malicious attackers or unintentional actions. Examples include:
- Phishing attacks that trick users into revealing credentials
- Ransomware deployed through malicious email links
- Disgruntled employees misusing access to sensitive systems
- Unpatched software exploited by cybercriminals
- Natural disasters like floods or fires that affect physical assets
Identifying the types of threats most relevant to your industry is the first step in building a meaningful risk profile.
Vulnerabilities
Vulnerabilities are the weaknesses or gaps in your systems, configurations, processes, or people that threats can exploit. Examples include:
- Outdated software with known security flaws
- Weak passwords or lack of multi-factor authentication
- Unsecured APIs in applications
- Untrained employees susceptible to social engineering
- Lack of network segmentation exposing critical data
Identifying vulnerabilities is crucial. Many breaches happen not because of new, sophisticated techniques but because of unaddressed basics.
Impact
Impact measures the potential consequences if a threat successfully exploits a vulnerability. Impacts can vary in severity and scope. Examples include:
- Financial loss from halted operations
- Regulatory fines for non-compliance with data protection laws
- Reputational damage causing customer attrition
- Intellectual property theft reducing competitive advantage
- Legal liability due to data exposure
Categorizing impacts and defining risk levels (e.g., low, moderate, high) can help prioritize risk mitigation efforts.
Likelihood
Likelihood refers to the probability that a specific threat will exploit a particular vulnerability. Organizations can use:
- Qualitative ratings such as Low / Medium / High
- Quantitative estimates (e.g., a 25% chance over 12 months)
- Historical data on incident frequency
- Industry threat reports and vendor insights
A high-impact risk that’s unlikely to occur may be treated differently than a moderate risk with a high likelihood.
Understanding the Risk Equation
To assess overall potential risk, many organizations use a simple formula:
Risk = Threat × Vulnerability × Asset Value
Example: Let’s say a company’s customer database is highly valuable. If it’s vulnerable due to weak access controls, and phishing is a known threat targeting the company, the resulting risk score would be high, even if no risk event has occurred yet.
This formula helps translate abstract concerns into measurable priorities.
Quantitative vs. Qualitative Risk Assessments
There’s no one-size-fits-all approach. Here’s a quick breakdown:
Quantitative Assessments
- Use numerical data to estimate risk in financial terms
- Support detailed cost-benefit analyses
- Require more data, tools, and expertise
- Best for mature organizations and financial planning
Qualitative Assessments
- Use descriptive categories (e.g., High, Medium, Low)
- Easier and faster to implement
- Useful when data is limited or decisions must be made quickly
- Often used in early-stage or smaller risk programs
Many organizations use a hybrid approach, starting with qualitative methods and refining with quantitative data over time.
9-Step Cybersecurity Risk Assessment Process
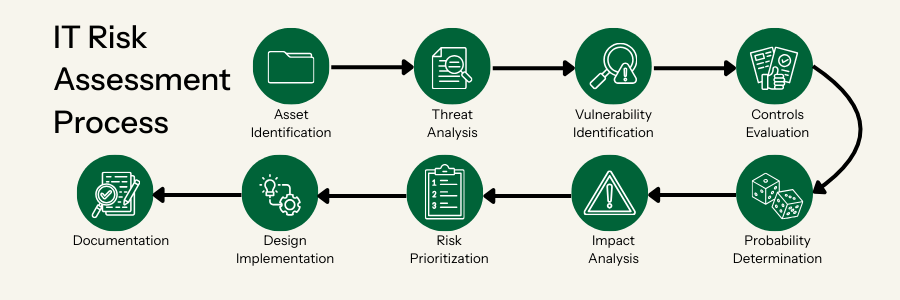
A thorough IT risk assessment is a comprehensive framework that involves more than just scanning for threats. It’s a strategic, step-by-step process designed to uncover risks, prioritize them, and implement effective safeguards. Here’s a breakdown of the nine essential steps to guide your efforts in 2025 and beyond.
1. Asset Identification and Classification
What it accomplishes: You can’t protect what you don’t know exists. This step creates a comprehensive inventory of all information assets, allowing you to focus protection efforts where they matter most.
How to perform it:
- Document all digital and physical assets: data, hardware, applications, cloud services, etc.
- Assign asset owners and a designated risk owner for accountability
- Categorize based on business impact
Tools/resources: Asset discovery tools like SolarWinds, Lansweeper, or Microsoft Defender for Endpoint
Common challenges: Overlooking shadow IT or third-party assets
Solution: Run regular scans and include all departments in reviews
Pro Tip: Focus on identifying your “crown jewels”. These are the systems and data most critical to your operations.
2. Threat Landscape Analysis
What it accomplishes: Pinpoints the types of cyber and physical potential threats most relevant to your organization.
How to perform it:
- Monitor industry-specific threat reports
- Identify likely adversaries and attack methods
- Factor in geopolitical and seasonal trends
Tools/resources: US-CERT alerts, ISAC threat intelligence feeds, Microsoft Security Reports
Common challenges: Information overload
Solution: Prioritize threats based on relevance to your assets and industry
Pro Tip: Keep in mind that in 2025, AI-driven phishing, deepfake-based social engineering, and supply chain attacks are among the top emerging threats.
3. Vulnerability Identification Strategies
What it accomplishes: Finds weak points that threats can exploit.
How to perform it:
- Run automated vulnerability scans (e.g., Nessus, Qualys)
- Perform manual penetration testing periodically to discover exploitable weaknesses
- Review system configs and code
- Evaluate employee behavior and training gaps
Tools/resources: OpenVAS, Burp Suite, internal audits, third-party penetration testing
Common challenges: Focusing only on technical vulnerabilities
Solution: Don’t ignore people, business processes, and physical access
Pro Tip: Include non-technical vulnerabilities like poor access controls, inadequate security policies, or lack of policy enforcement.
4. Security Controls Evaluation
What it accomplishes: Assesses how effective current defenses and security processes are and where the gaps lie.
How to perform it:
- Map existing controls to frameworks (e.g., NIST CSF, ISO 27001)
- Use gap analysis to highlight missing or ineffective controls
- Test controls through simulated attacks, tabletop exercises, or audits
Tools/resources: Control mapping tools, NIST CSF 2.0, Excel-based gap templates
Common challenges: Outdated or redundant controls
Solution: Regularly review for relevance and update accordingly
Pro Tip: Use a simple spreadsheet to track each control, its purpose, responsible owner, and test frequency.
5. Probability Determination
What it accomplishes: Estimates the likelihood of a risk materializing.
How to perform it:
- Assign qualitative scores (High, Medium, Low) or quantitative percentages
- Factor in threat actor motivation, asset exposure, and historical security incidents
Tools/resources: Historical incident logs, threat intel databases, stakeholder input
Common challenges: Guesswork without data
Solution: Leverage available breach history and incident data
Pro Tip: Use a standard scale, such as 1–5 or percentage likelihood, for consistency in comparisons.
6. Impact Analysis Methods
What it accomplishes: Estimates the potential damage a successful exploit could cause.
How to perform it:
- Evaluate four dimensions of impact:
- Financial (e.g., fines, lost revenue)
- Operational (e.g., downtime)
- Reputational (e.g., customer loss)
- Strategic (e.g., missed opportunities)
- Use BIA (Business Impact Analysis) templates to structure your findings
Tools/resources: Business continuity plans, finance reports, customer sentiment surveys
Common challenges: Underestimating intangible impacts
Solution: Include legal and PR team input
Pro Tip: Even “low-risk” systems can have high-impact consequences if tied to customer experience or compliance.
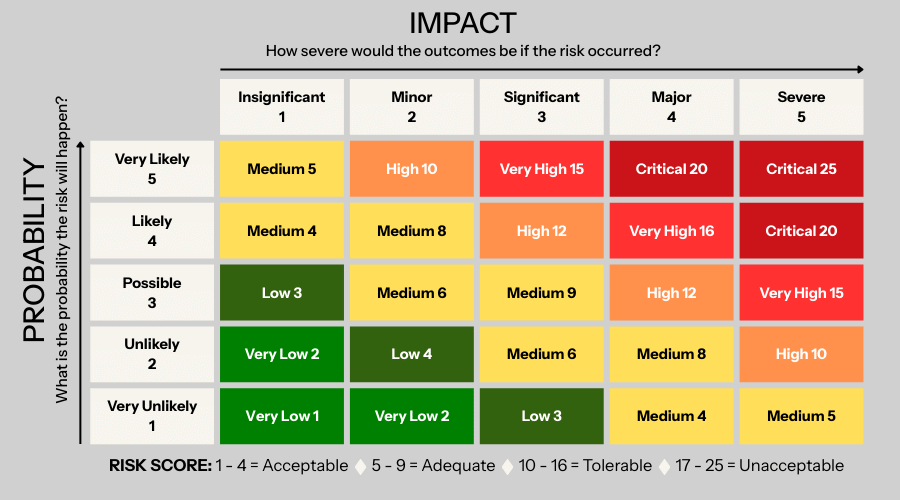
7. Risk Prioritization Techniques
What it accomplishes: Ranks potential risks based on impact and likelihood so you know where to act first.
How to perform it:
- Use a 5×5 risk matrix to determine the inherent risk score
- Generate a heat map to visualize critical risks
- Include stakeholders and senior management to ensure alignment
Tools/resources: Excel or Power BI for heat map visualization
Common challenges: Too many high-priority risks
Solution: Introduce additional tiers or review thresholds
Pro Tip: Use color-coded risk matrices to communicate clearly with executives.
8. Control Design and Implementation
What it accomplishes: Implements the right actions to reduce risk to acceptable levels.
How to perform it: Choose one or more of the following treatments:
- Accept: If cost of mitigation > potential impact
- Avoid: Discontinue risky activities
- Transfer: Use insurance or outsource (e.g., MSSP)
- Mitigate: Add new controls or enhance existing security measures
Tools/resources: Control catalogs (NIST, CIS Controls), project plans that address residual risk
Common challenges: Overengineering or slow implementation
Solution: Prioritize by risk score and resource availability
Pro Tip: Create a simple roadmap showing short-, mid-, and long-term actions to build momentum.
9. Documentation
What it accomplishes: Maintains accountability and supports audits, tracking, and improvements.
How to perform it:
- Create a risk register listing each risk, score, owner, treatment, and status
- Document treatment plans, timelines, and test results
- Schedule regular reviews
Tools/resources: Governance, Risk & Compliance platforms (e.g., LogicGate, RiskWatch), risk assessment template, or custom Excel templates
Common challenges: Incomplete or outdated documentation
Solution: Assign owners and automate review reminders
Pro Tip: Monitor key risk indicators (KRIs) to flag when risks are changing.
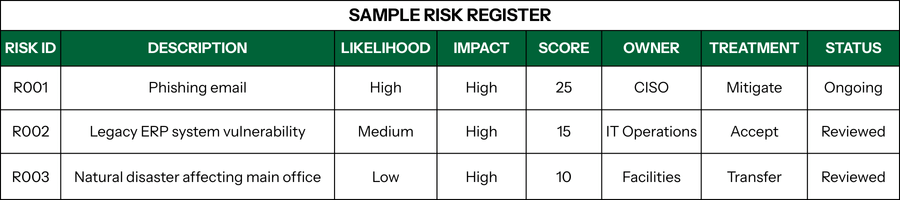
IT Risk Assessment for Specific Compliance Frameworks
Many compliance frameworks have unique requirements related to IT risk assessments. Understanding these nuances is key to aligning your cybersecurity practices with legal and regulatory expectations. Below are several major frameworks and how they incorporate risk assessments into their compliance models.
NIST Cybersecurity Framework (CSF) 2.0
The NIST CSF 2.0 emphasizes risk assessment as a foundational activity under the “Identify” function. Specifically, it requires organizations to:
- Identify threats, potential vulnerabilities, and potential impacts to organizational operations
- Maintain a comprehensive risk management process and strategy
- Assess organizational risk tolerance and prioritize activities accordingly
Documentation needed:
- Risk assessment reports
- Risk tolerance policies
- Control mapping to CSF subcategories
Frequency:
- At least annually, or more often, depending on risk posture
Common challenge:
- Translating technical risks into business risks
Solution: Use business impact analysis (BIA) techniques to communicate effectively with leadership
ISO/IEC 27001
ISO 27001 treats risk management as the core of its Information Security Management System (ISMS). Under Section 6, organizations must:
- Define a methodology for risk identification, analysis, and treatment
- Maintain a risk treatment plan
- Select controls from Annex A based on risk profile
Documentation needed:
- Risk assessment methodology
- Risk register
- Statement of Applicability (SoA)
Frequency:
- Risk assessments must be updated regularly and during major changes to the ISMS
Common challenge:
- Keeping the SoA current with actual controls
Solution: Use automated tracking tools to align implementation with documentation
CMMC 2.0
The Cybersecurity Maturity Model Certification (CMMC) 2.0 introduces tiered requirements for DoD contractors:
- Level 1: Basic safeguarding with annual self-assessments
- Level 2: Advanced security practices, including documented risk assessments aligned with NIST SP 800-171
- Level 3: Expert-level security and third-party audits
Documentation needed:
- Risk assessment reports
- Security System Plan (SSP)
- Plan of Action & Milestones (POA&M)
Frequency:
- Annually for Levels 1 & 2; more frequent for Level 3 or as dictated by the DoD
Common challenge:
- Understanding control maturity expectations
Solution: Work with a Registered Provider Organization (RPO) to ensure alignment
Industry-Specific Frameworks
HIPAA (Healthcare)
HIPAA mandates that covered entities and business associates perform periodic risk analyses of systems handling protected health information (PHI). Organizations must:
- Identify threats to the confidentiality, integrity, and availability of PHI
- Implement risk mitigation strategies
Documentation:
- Risk analysis reports
- Administrative, physical, and technical safeguards
Common challenge:
- Treating HIPAA risk assessments as one-time efforts
Solution: Build assessments into regular security review cycles
PCI DSS (Payment Card Industry)
The PCI DSS standard requires entities handling payment card data to perform annual risk assessments and after significant changes. Organizations must:
- Identify critical assets that store, process, or transmit cardholder data
- Map and test controls to relevant requirements
Documentation:
- Risk assessments
- Network diagrams
- Control effectiveness testing records
Common challenge:
- Underestimating the scope of the cardholder data environment (CDE)
Solution: Conduct detailed asset discovery and segmentation reviews
GLBA (Financial Sector)
Under the Gramm-Leach-Bliley Act, financial institutions must have a written information security plan that includes:
- Ongoing risk assessment of customer information systems
- Evaluation of internal and external threats
- Monitoring of service provider practices
Documentation:
- Information Security Program (ISP)
- Risk assessment reports
- Vendor due diligence documentation
Common challenge:
- Inconsistent vendor risk management
Solution: Incorporate third-party risk into broader assessment processes
Conclusion and Next Steps
As cyber threats grow in frequency and sophistication, IT risk assessments are no longer optional—they’re essential for maintaining a strong security posture. From ransomware attacks and insider threats to regulatory crackdowns, businesses today face an ever-changing risk landscape. A structured assessment process empowers organizations to stay ahead, allocate resources wisely, and build resilience.
Your 30-60-90 Day Roadmap
Next 30 Days:
- Build or update your IT asset inventory
- Identify “crown jewel” systems and data
- Schedule a kickoff meeting with key stakeholders
Next 60 Days:
- Conduct a threat and vulnerability assessment
- Evaluate current controls and identify gaps
- Prioritize risks using a matrix or heat map
Next 90 Days:
- Begin implementing risk treatments
- Document your risk register and treatment plans
- Set a recurring review schedule for ongoing assessment
5 Immediate Actions to Take Today
- Audit your most critical assets
- Create a simple risk matrix for leadership visibility
- Evaluate your top three security controls for effectiveness
- Book time on the calendar for a formal risk review
- Educate your team—risk awareness is everyone’s job
“Cybersecurity is not a one-and-done exercise. Risk assessments are the compass that guides your strategy in an unpredictable world.” — IBM Security, 2024 Cost of a Data Breach Report
By making IT risk assessments a routine and proactive part of your operations, you not only strengthen your defenses, but you also position your organization for smarter decisions and sustainable growth.